You have created and encrypted a volume or container and want to create a hidden encrypted volume within it. You should remember that it is impossible to prove that such a volume exists.
If there is no encrypted volume or container it is very easy to create one with the help Cryptic Disk. Just go through the instructions:
How to Create an Encrypted Container
How to Encrypt a Volume
Now there is an encrypted volume (or a container). It has to be unmounted before turning it into a hidden encrypted volume.
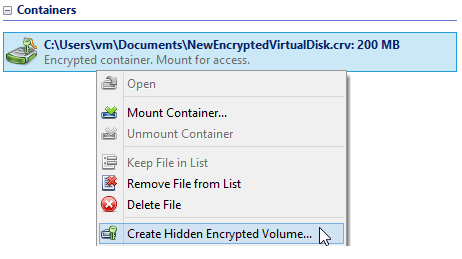
Choose the encrypted volume (or container. Note: further the guide will deal with the volume) in the main window. Start the hidden encrypted volume creation wizard.
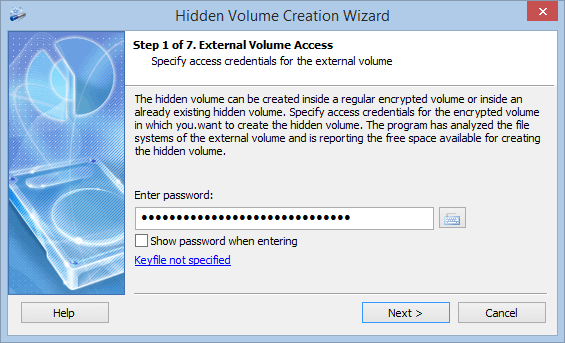
In the first step specify the access parameters (a password and/or key files) for the encrypted volume inside which the wizard will create a hidden encrypted volume.
The software will analyze the file system of the encrypted volume and spot the unused volume sections (not used by files), then calculate their maximum volume (total size of the free sections) of the hidden encrypted volume.
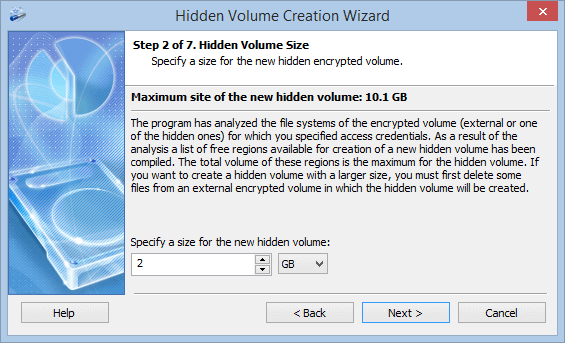
You can decrease the size of the hidden encrypted volume to be created. But let’s leave the proposed volume as is and proceed.
All the rest of the wizard steps are the same as for the encrypted container or physical volumes creation wizards. You can check the guide for them at How to Create an Encrypted Volume.
The hidden encrypted volume is successfully created!
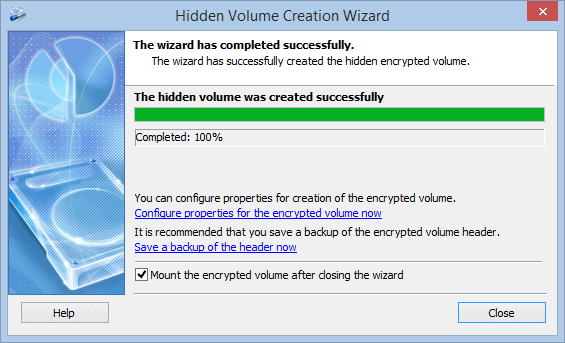
It is very easy to work with the hidden encrypted volumes. After mounting you can work with it as with an ordinary volume.
To mount a hidden encrypted volume, enter the password that you specified when creating it.
To mount an encrypted volume (or a container) inside which there is a hidden encrypted volume enter the password that was used for this “external” (unhidden) encrypted volume (or a container). It means that you enter one password and one encrypted volume is mounted or you enter the other password and the other encrypted volume is mounted. So it depends on the entered password which encrypted volume is a hidden one. Sometimes it is quite convenient.
When working with the mounted encrypted volumes inside which there are hidden encrypted volumes you should take up some precautions. The thing is that the software is not aware of any hidden encrypted volumes (that is the essence of hiding them encrypted so that it is not possible to prove their existence). So the software is not aware what sections of the mounted encrypted volume contain a hidden encrypted volume. When writing files to this volume they can overwrite these sections and damage the hidden encrypted volume.
To protect the hidden encrypted volume against any damage go to the advanced options (the “More…” button in the mounting window) and enable the “Protect nested hidden volumes from damage when writing to mounted volumes” option when mounting an “external” encrypted volume (with the nested hidden one).
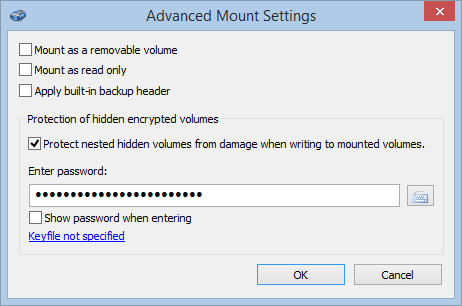
Enter the password to the hidden encrypted volume. In this case the software will detect all the taken sections of the hidden encrypted volume and block all the attempts to write in them. It means that the hidden encrypted volume in this case will remain intact.