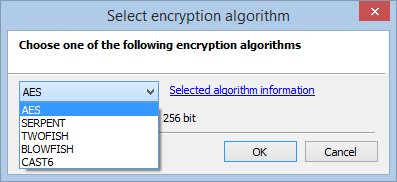
Cascade Encryption
Cryptic Disk allows you to use several algorithms in combination to provide the strongest possible encryption of a container or a drive. To begin with, data is encrypted using one algorithm, the result is then encrypted using another, and so on. A separate encryption key is used for each algorithm, greatly boosting the strength of the protection.
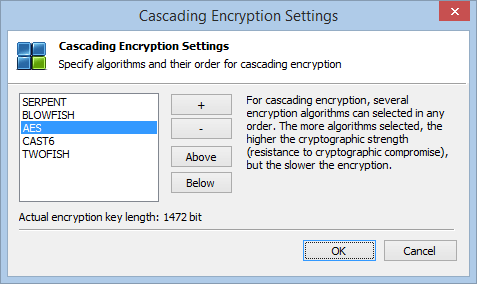
In XTS mode, there are two different encryption keys for each algorithm, generating a key that is twice as long. With all encryption algorithms in XTS mode, encryption keys have a length of 2,944 bits.