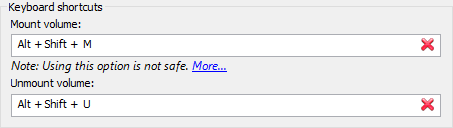
Hot Keys
- Hot keys can be assigned to instantly mount and unmount encrypted drives.
- Different combinations can be assigned to different containers and drives.

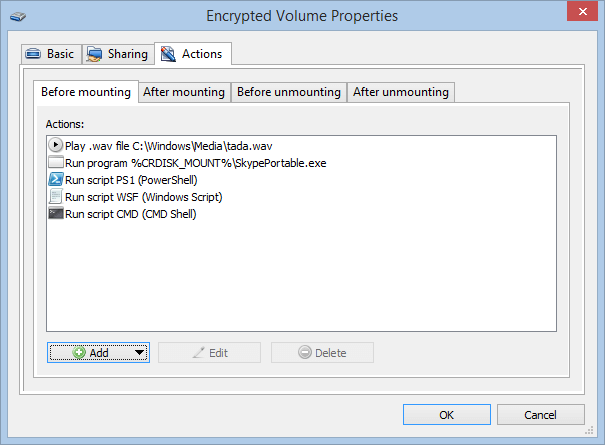
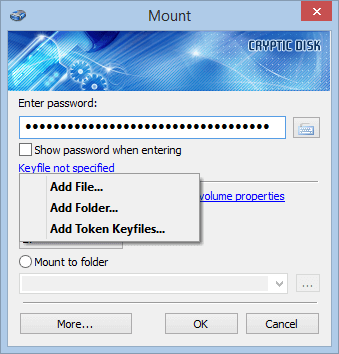
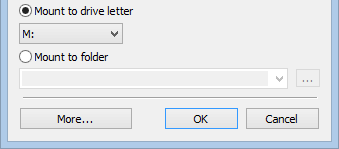
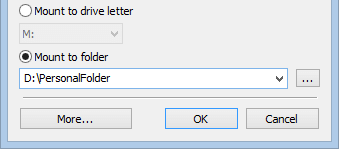


Cryptic Disk offers the option of mounting and unmounting drives from the command line.
As well as built-in support for running programs and scripts, the command line in Cryptic Disk allows you to use automation scripts to work with encrypted drives and data on them.